Real-Time Fine-Tuning of the WAF via API
This article was originally published on Sucuri blog (read here).
Though the Sucuri Firewall is simple to set up and protects your website immediately, it’s possible to have granular control of the WAF by using an API.
For instance, there’s a specific filter inside the WAF dashboard called Emergency DDoS. This filter basically increases the strength of the DDoS protection to an “emergency” level where most non-human access is blocked.
API to Boost Firewall Protection
The Firewall API is mostly used for whitelisting and clearing the website cache. Nevertheless, it is a great way to leverage the API to increase the website protection in case you face a big DDoS attack. The Sucuri Firewall will take more than a few minutes to stop automatically.
Ideally, you should not leave the “Emergency DDoS” filter enabled all the time as it can be burdensome due to its side effects. When the Emergency DDoS filter is on, all requests will go through the filter. For example, it would make Google Analytics believe the traffic is direct instead of organic. The filter might also block third party integrations. However, you can create a script on the server to enable that filter only when strictly necessary.
The best way to check if your server is receiving more requests than it’s able to handle would be by checking the numbers of concurrent requests being processed by the web server, the number of 50x requests, the resource usage of the server, etc and only then trigger any change on the WAF API.
If a few of those checks return negative, then the script would trigger the API to enable the “Emergency DDoS” filter.
Emergency DDoS Filter
For demonstration purposes, let’s use the “netstat” command to count the number of https requests on the servers and trigger the API if the number of connections reaches 500. This is a simple test, so be sure to use a more suitable and reliable check.
Using Bash, here is the script:
#!/bin/bash # Trigger Emergency DDoS if number of https requests reaches 500 if [[ "$(netstat | grep https | wc -l)" -ge "500" ]]; then curl https://waf.sucuri.net/api?v2 -d "k=API_KEY&s=API_SECRET&a=update_setting&http_flood_protection=js_filter" fi
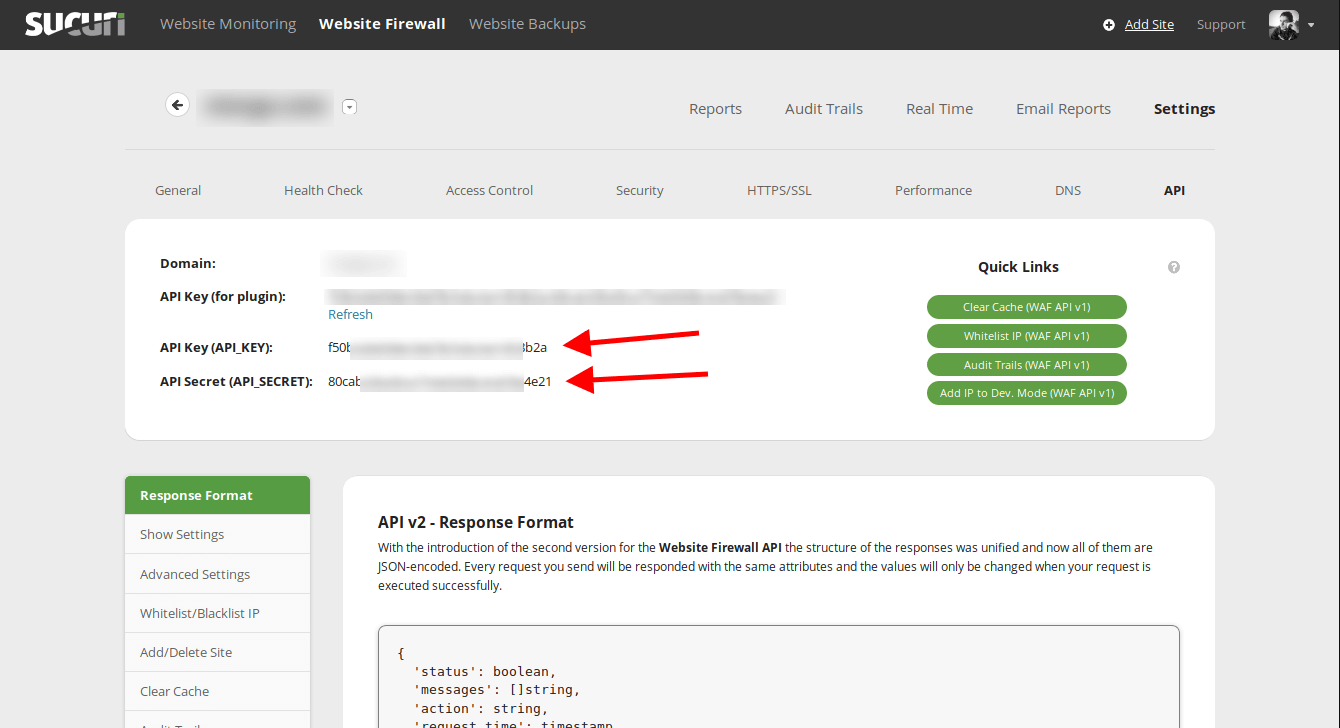
Update “API_KEY” and “API_SECRET” with your credentials (available at WAF dashboard -> API).
Save the script as “emergencyddos.sh” and then configure a cron job to run, let’s say every 2 minutes. That way if the server ever reaches the 500 https connections mark, the Emergency DDoS filter would be activated.
You can improve the script to have a “smarter checking” by:
- disabling the Emergency DDoS protection after 1h;
- using Protected Page with Captcha Protection;
- activating other filters such as “Aggressive bot filter”;
- adding a new hosting IP to keep up with the growing traffic.
Let’s say you want to trigger the “Aggressive bot filter” as well. Just add a new curl request to the API triggering that filter after enabling the “Emergency DDoS filter”:
#!/bin/bash # Trigger Emergency DDoS and Aggressive bot filter if number of https requests reaches 500 if [[ "$(netstat | grep https | wc -l)" -ge "500" ]]; then curl https://waf.sucuri.net/api?v2 -d "k=API_KEY&s=API_SECRET&a=update_setting&http_flood_protection=js_filter" curl https://waf.sucuri.net/api?v2 -d "k=API_KEY&s=API_SECRET&a=update_setting&aggressive_bot_filter=enabled" fi
Today, we are going to have a webinar on what can be done with our API to make your life easier and more automated. Register for a free seat here.
Conclusion
The WAF API will allow you to write all kinds of triggers, import SSLs into the WAF, or even set the website into a total read-mode only (security level paranoid). It’s up to you.
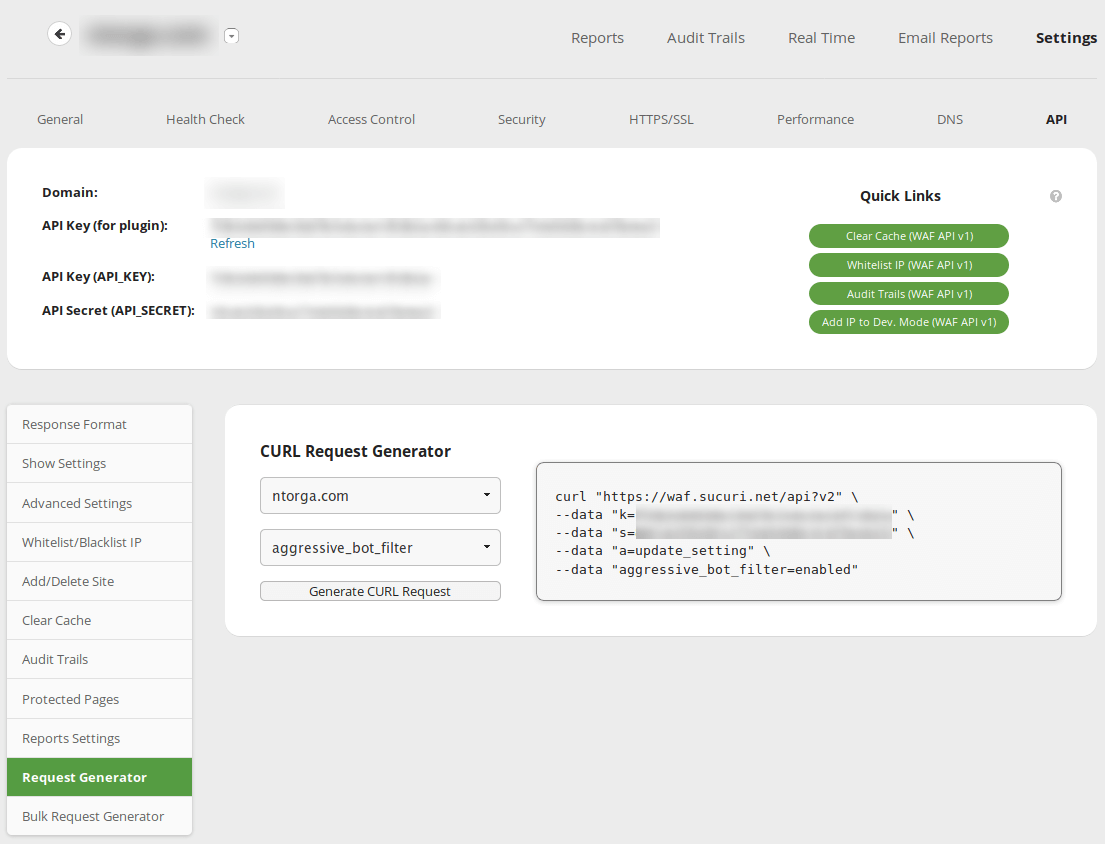
To make this process a bit easier, the WAF offers a tool called “Request Generator”. It gives you precisely the curl request needed.
Allow the creative developer inside you decide how to save more time and improve your website stability with the Sucuri Firewall.
Comments